The Future of Enterprise Browsing
Bundle enterprise-grade security with the most elegant user experience
Oasis: The Evolution of Browsing
The definition of a "browser" has fundamentally changed in recent years. What was once simply a tool for viewing web pages has evolved into something far more powerful and intelligent. This transformation has been driven by two major innovations: enterprise browsers like Island's security-focused platform, and AI browsers such as Perplexity's Comet, OpenAI's Atlas, GenSpark, and Dia that integrate artificial intelligence directly into the browsing experience.
Oasis represents the convergence of these two revolutionary approaches. It is both an enterprise browser and an AI browser, combining the security and control that modern organizations demand with the intelligence and automation that users expect from next-generation software. This dual nature makes Oasis uniquely positioned to address the complex challenges of today's digital workplace.
In this guide, we'll break down what makes Oasis so special. We'll explore how it provides enterprise security, how its AI capabilities transform productivity, and why it represents the future of how we interact with the web. Whether you're evaluating enterprise browser solutions or looking to understand the next evolution of web technology, this guide will provide the insights you need to make informed decisions.
Tools for any role
Core Oasis commands that adapt to your workflow
Oasis core commands like "open new tab", "organize windows", and "group tabs" can be customized and adapted to serve any role. The same powerful tools work for everyone—just configured differently.
Core Commands
Sales
Marketing
Research & Analysis
Development
Your Workflow
What is Oasis?
Understanding Oasis as both enterprise and AI browser
Oasis represents the convergence of enterprise browser security and AI-powered intelligence. It combines the security and control that modern organizations demand with the intelligence and automation that users expect from next-generation software.
Free Agentic Browser
Designed for personal productivity with AI-powered assistance and smart organization tools.
Enterprise Browser
Built for enterprise environments with enhanced security, compliance, and collaboration features.
Designed for How Your Mind Works
Unlike other AI browsers that create more complexity with multiple agents and tabs, Oasis is designed to fit the way your mind naturally works. We pay attention to the "little things" that matter in your spatial workspace.
While other solutions create multiple agents that require constant clicking between different interfaces, Oasis lets you view all agents in one unified page, eliminating the tab chaos that plagues traditional AI browsers.
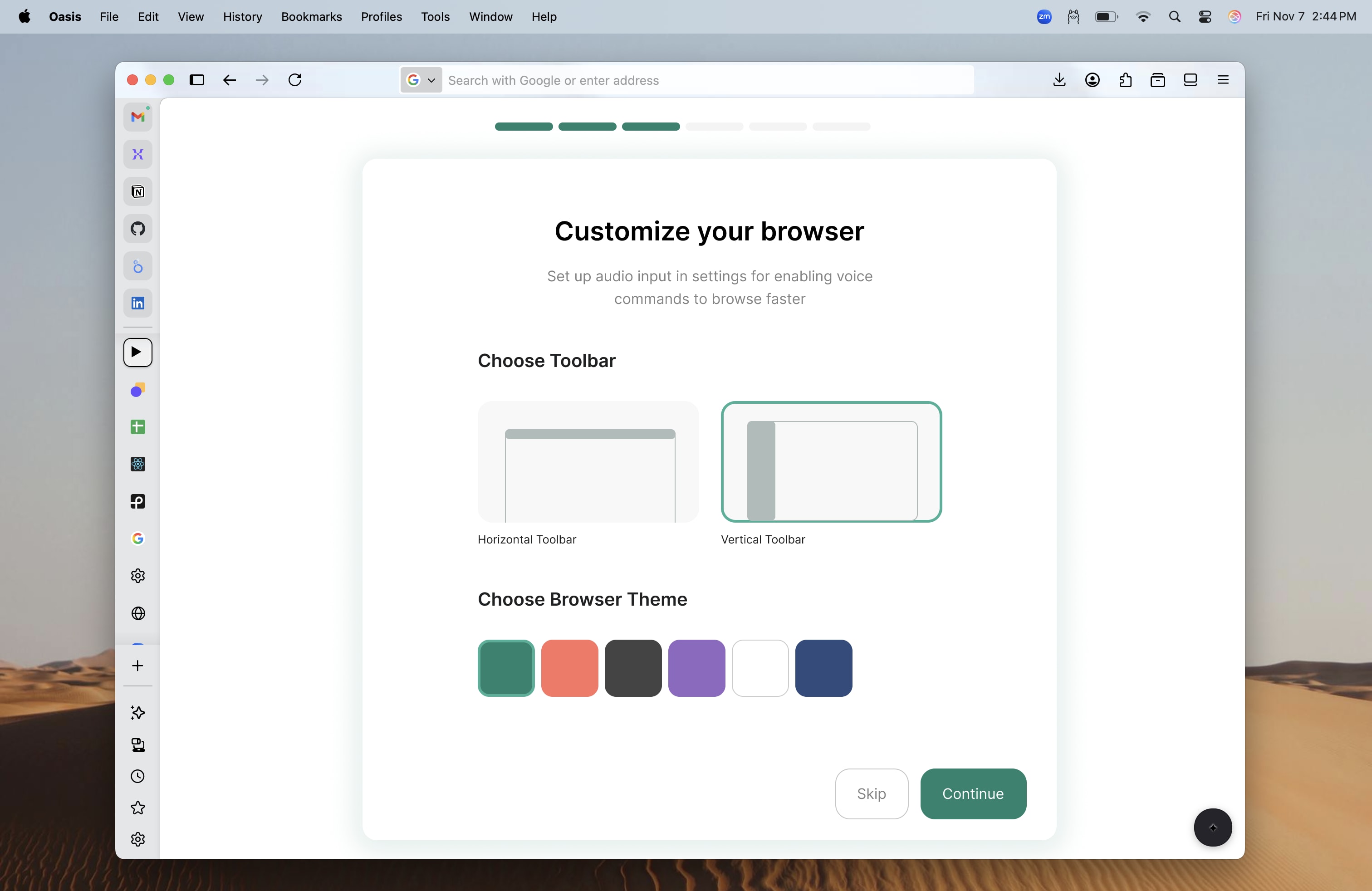
Deep AI Integration
AI commands are deeply rooted into the core of the browser, not bolted on as an afterthought. You can control everything from opening new windows to saving all tabs into organized hubs, extracting insights from research collections, all through natural language prompts or voice commands.
This seamless integration reduces friction and makes AI truly useful rather than just a novelty. The AI understands context, learns from your usage patterns, and adapts to your workflow.
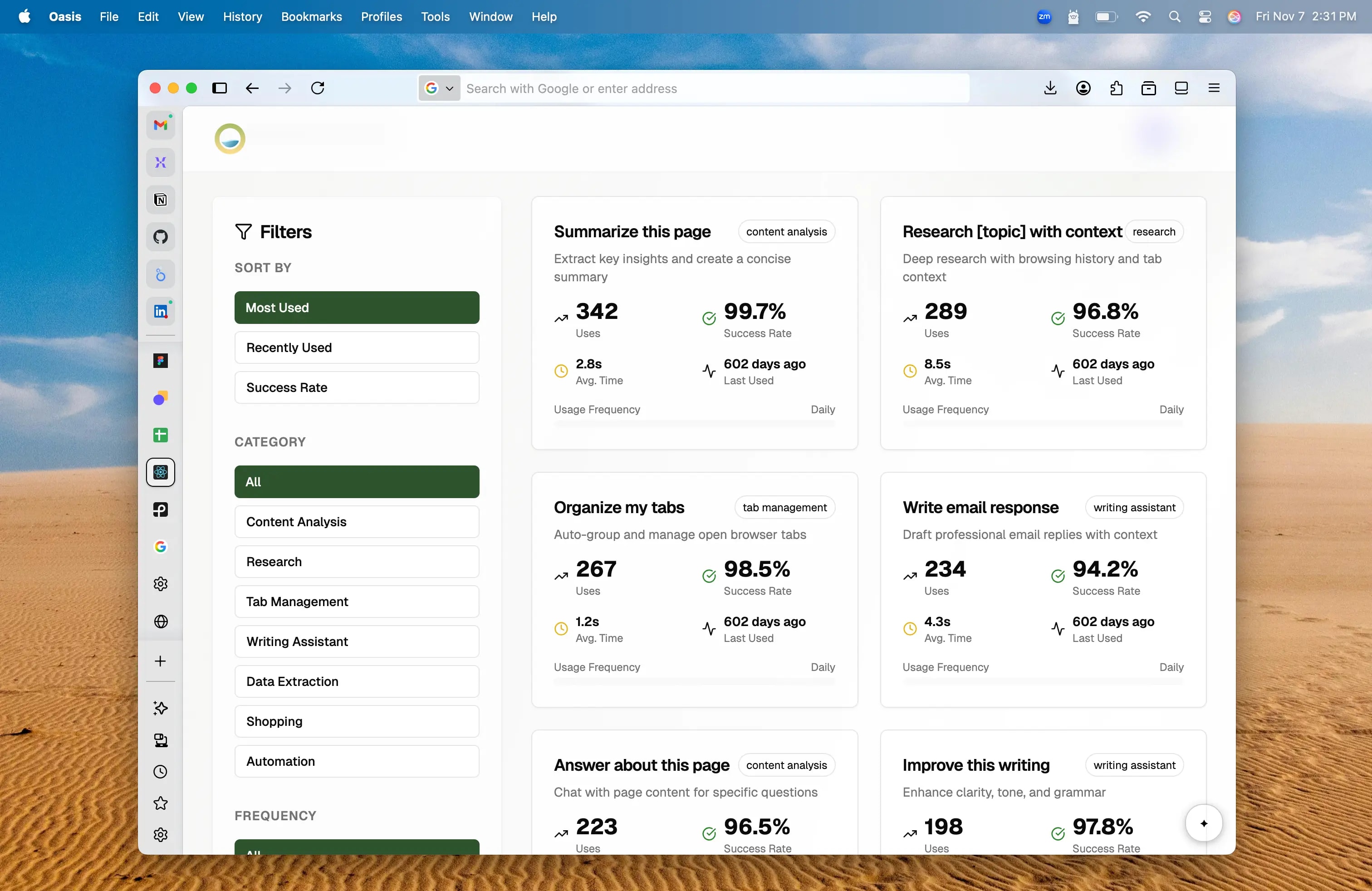
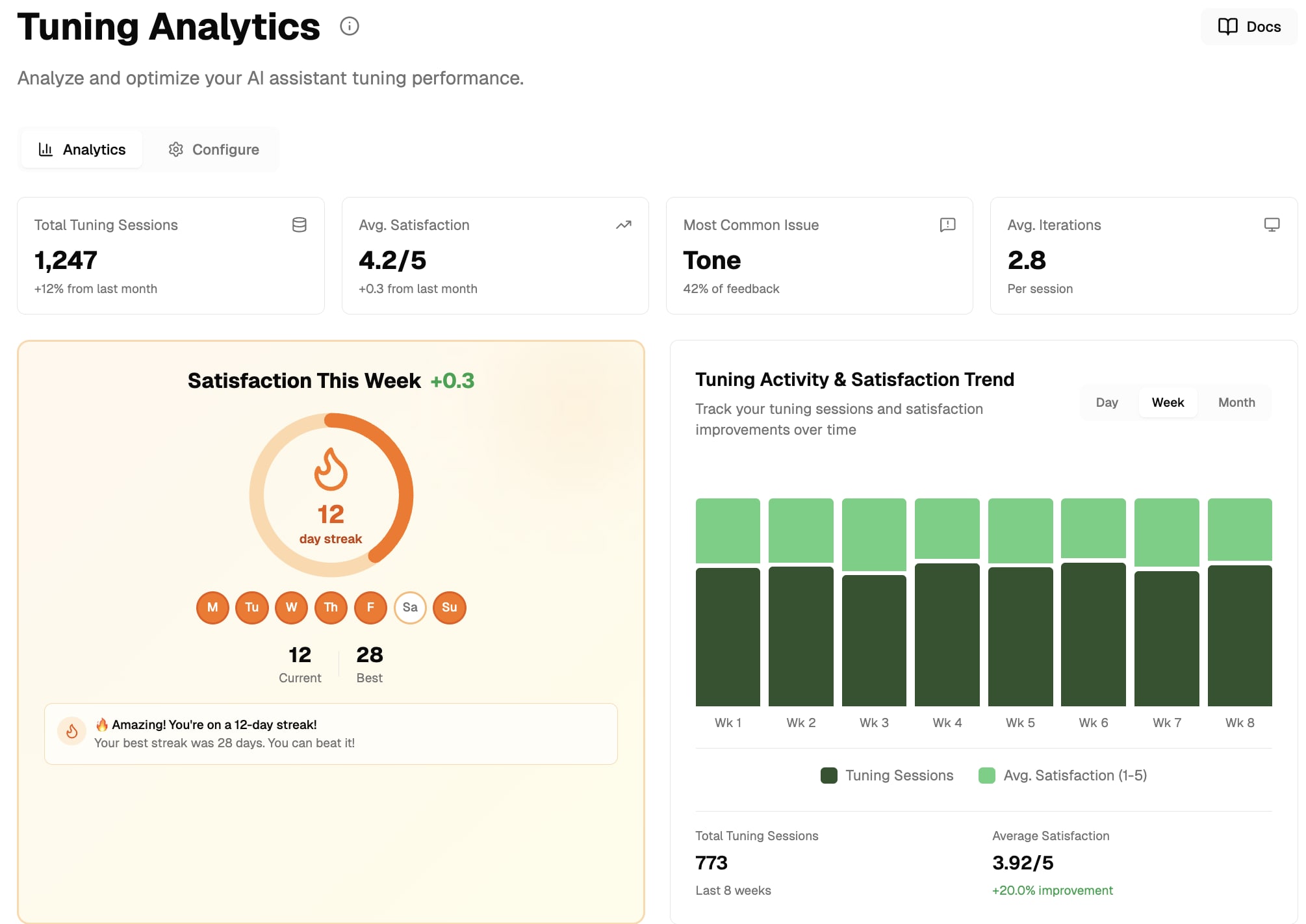
Trainable AI Companion & Security-First Design
One of the biggest issues with AI browsers like Perplexity's Comet is that they're slow, you can't monitor agents simultaneously, and commands often don't work as expected. Oasis includes training and gamification elements that let you fine-tune your own AI assistant, making it faster and more accurate for your specific needs.
You maintain control over your AI's learning and behavior. Additionally, maintaining security within an AI browser presents unique challenges that we specialize in solving.
Benefits of Oasis
Key advantages of choosing Oasis for your organization
Enterprise browsers provide stronger security, more control, and better visibility than consumer browsers, while also improving user productivity and reducing IT complexity.
Enhanced data protection and DLP (controls on copy/paste, download, printing, screenshots, watermarking).
Built‑in threat detection and prevention for phishing, malware, risky sites, and malicious downloads.
Zero trust access to SaaS and internal web apps directly from the browser, often replacing or reducing VPN and VDI.
New ergonomic workflows that adapt to how you work, with spatial organization and intuitive controls that reduce cognitive load and improve focus.
Simplified IT operations by consolidating multiple security agents and web security products into the browser layer.
Lower infrastructure and licensing costs by reducing reliance on legacy VPN, VDI, and separate web gateways.
Zero Trust Security
An enterprise browser can be used to implement a zero trust security framework across a wide range of deployment scenarios. User identity is verified with IdP integration and multi-factor authentication. Device posture is checked to verify the device meets security standards. Network and geolocation are examined to see where the request is coming from.
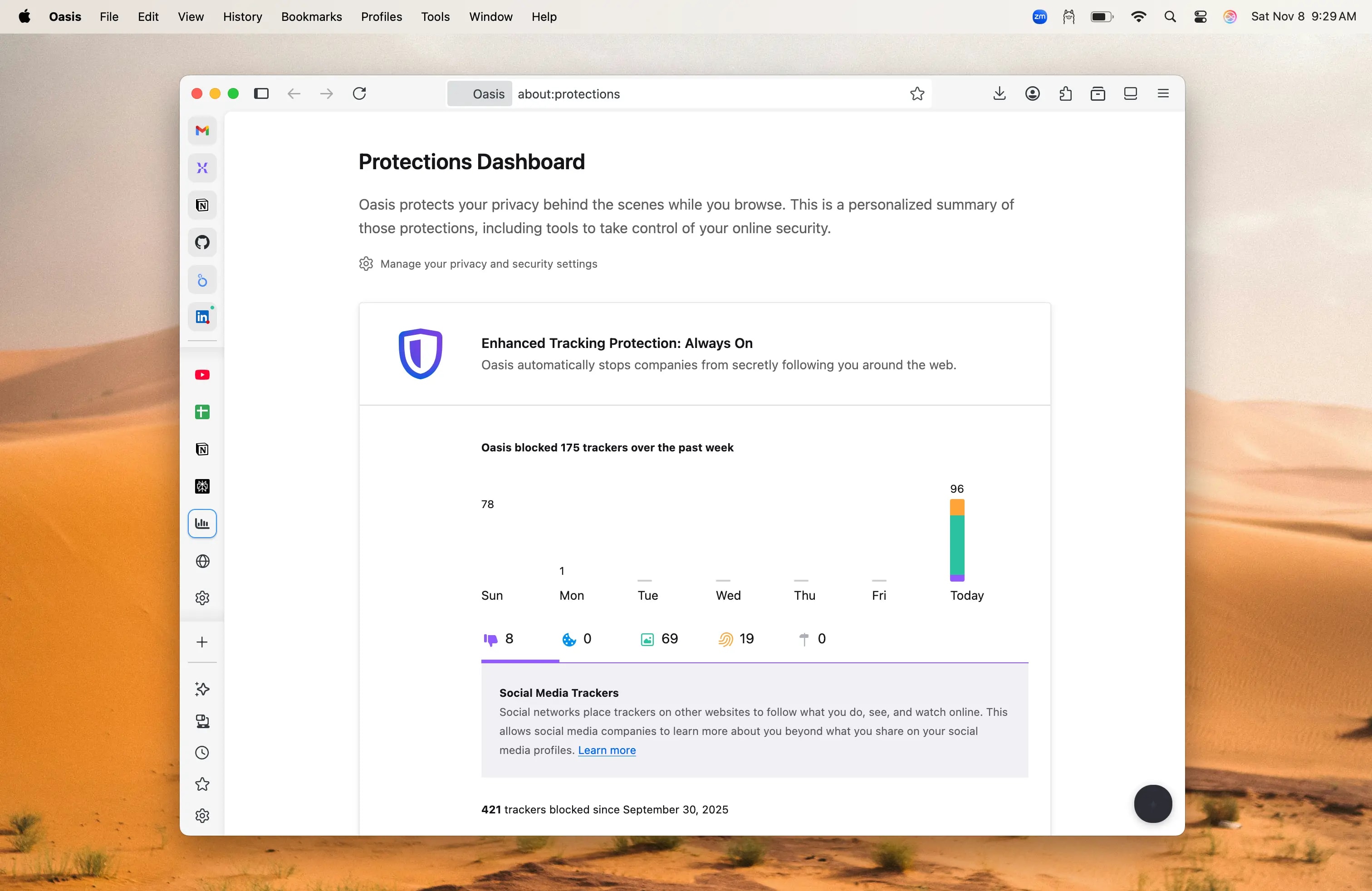
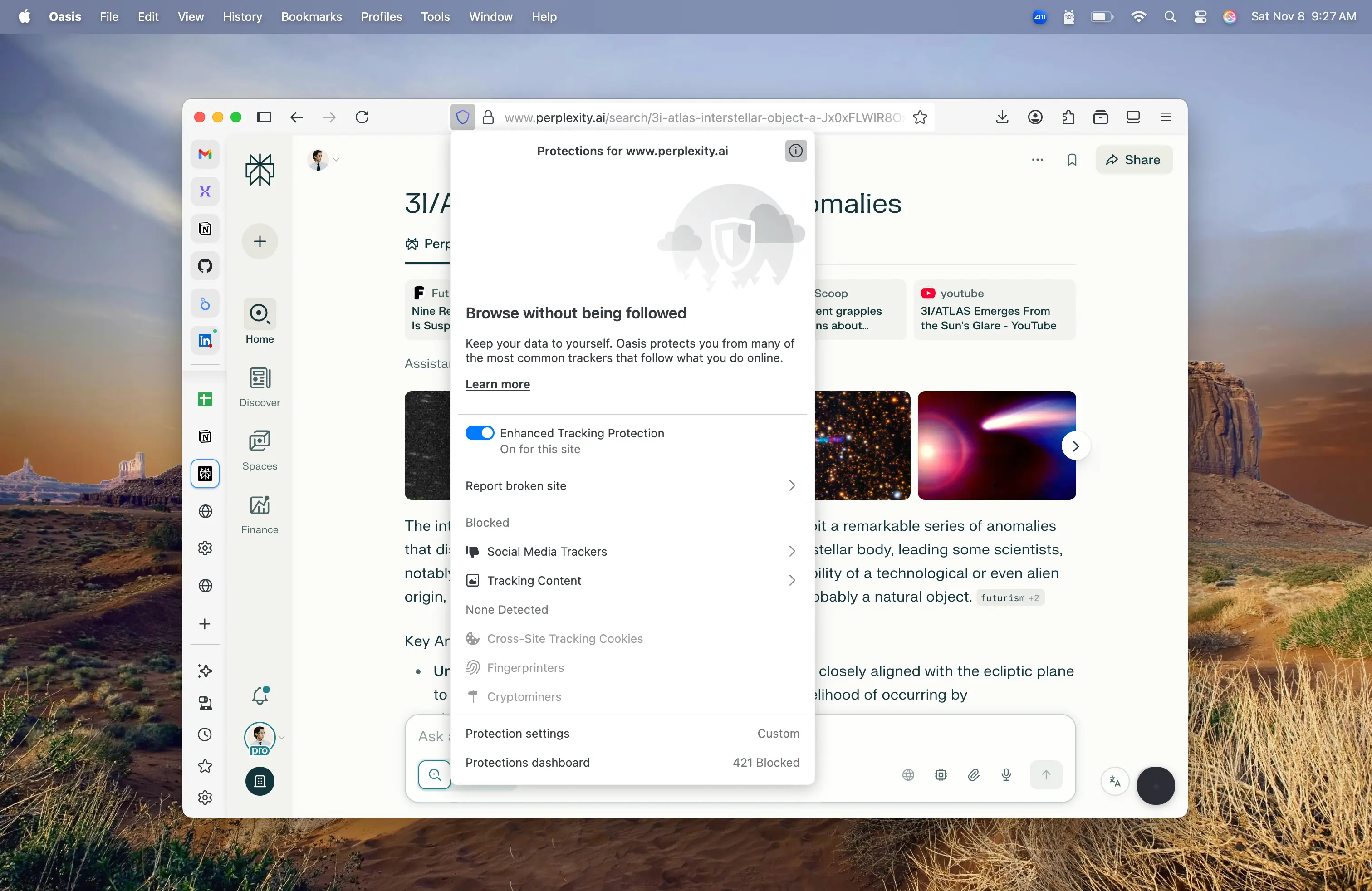
Safe Browsing & Threat Protection
An enterprise browser comes embedded with powerful security tools that protect all browser activity from the myriad of web-born threats, regardless of device or network. Malware is detected and blocked before ever reaching the endpoint. Phishing attacks are stopped before credentials are compromised. Unsafe or inappropriate sites are blocked from access.
Data Protection & DLP
An enterprise browser builds dynamic data protections into the browser itself, enabling you to build policies that prevent data leakage without disrupting organizational workflows. Its data loss prevention (DLP) controls protect sensitive data from being improperly downloaded or uploaded before it leaves or enters the browser.

Visibility & Monitoring
An enterprise browser offers unprecedented visibility into all browser activity in a way that simply wasn't possible before. Most legacy security tools offer visibility via network traffic inspection by decrypting SSL traffic. An enterprise browser offers visibility into browser behavior without any unnatural network traffic manipulation.
Single Sign-On
Seamless authentication with your existing identity providers
Key Points
- Works with Okta, Azure AD, Ping
- Built-in MFA support
- Seamless user experience
Similar browser vendors
How Oasis compares to other enterprise browser solutions
When evaluating enterprise browser solutions, it's important to understand how Oasis compares to other options in the market. The browser landscape has evolved significantly with the emergence of enterprise-focused solutions and AI-powered browsers.
Below is a comprehensive comparison of browser solutions, including enterprise browsers like Island and Talon, traditional enterprise browsers like Chrome Enterprise and Edge, and emerging AI browsers. This comparison will help you understand where Oasis fits in the competitive landscape and what makes it unique.
Browser Comparison
Use the Controls button to pin browsers for side-by-side comparison.
Centralized Control
Unified management console for enterprise-wide deployment
Deployment experience
What to expect when deploying Oasis in your organization
Oasis deployment follows a practical, incremental approach that prioritizes immediate functionality over complex initial configuration. The browser works out-of-the-box, allowing you to get users productive quickly while building security policies and configurations over time. This approach delivers tangible value within days rather than requiring months of setup and planning.
Integrate with your existing identity infrastructure
Oasis seamlessly connects with your current identity provider using industry-standard protocols including SAML, OAuth, and SCIM for user provisioning and authentication.
Distribute Oasis to your team
Deploy through your existing device management platform (VMware Workspace ONE, Citrix Endpoint Management, etc.) or provide a secure download link for self-service installation. The process is straightforward: download, install, and start using.
Users get up and running immediately
Team members authenticate through your existing identity system and can instantly import their bookmarks, saved passwords, and browser preferences for a familiar experience.
Gradually implement security policies
Begin with a pilot group and specific applications to develop policies that match your workflows. As you gain experience, expand to additional teams and use cases to build comprehensive security coverage.
Why This Approach Works
Ready-to-use browser eliminates lengthy setup processes
Users can be productive while policies are being developed
Rapid time-to-value with measurable results in days
Phased rollout reduces risk and allows for learning and adjustment
User Experience
Experience how Oasis feels to use day-to-day
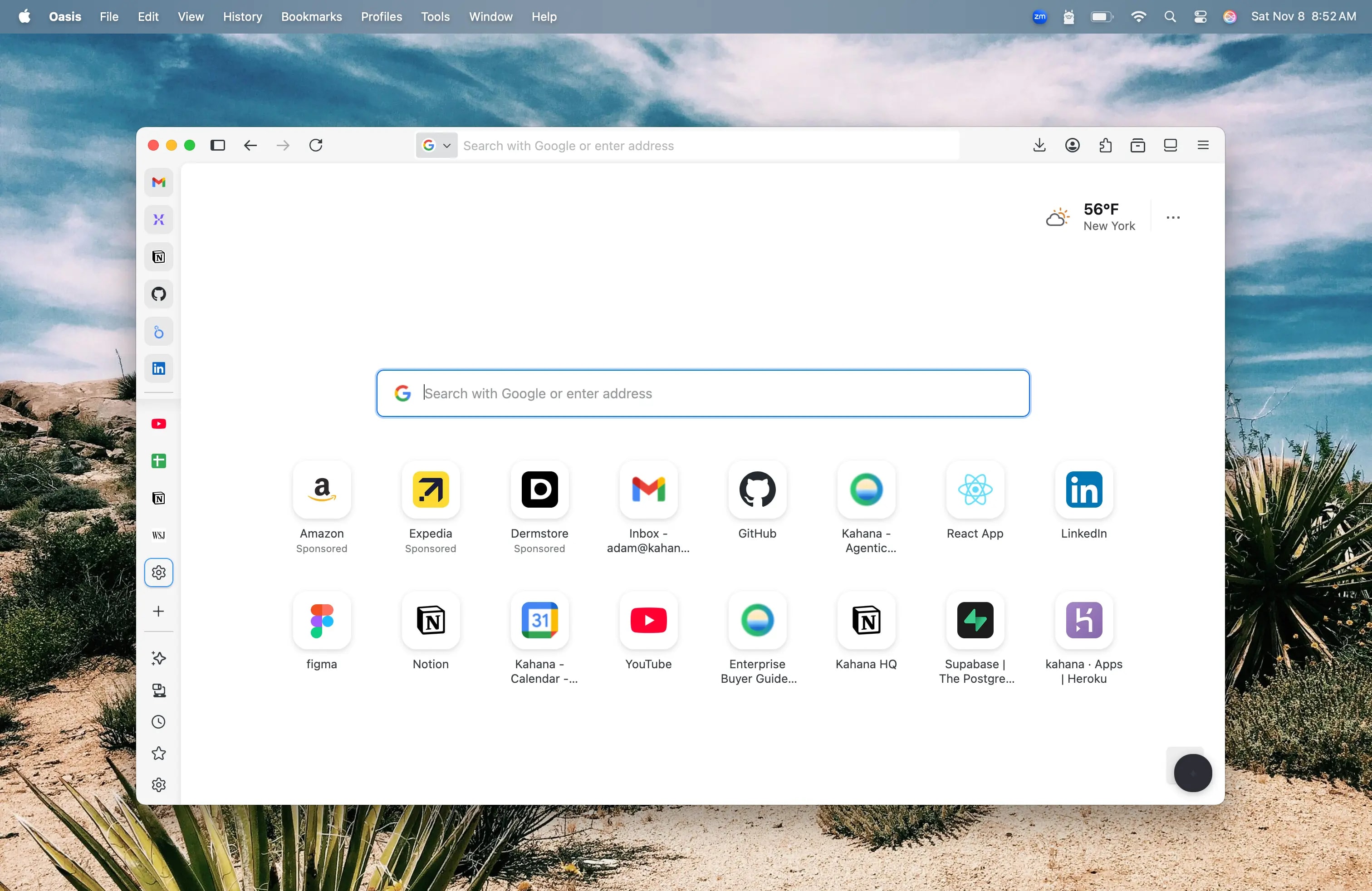
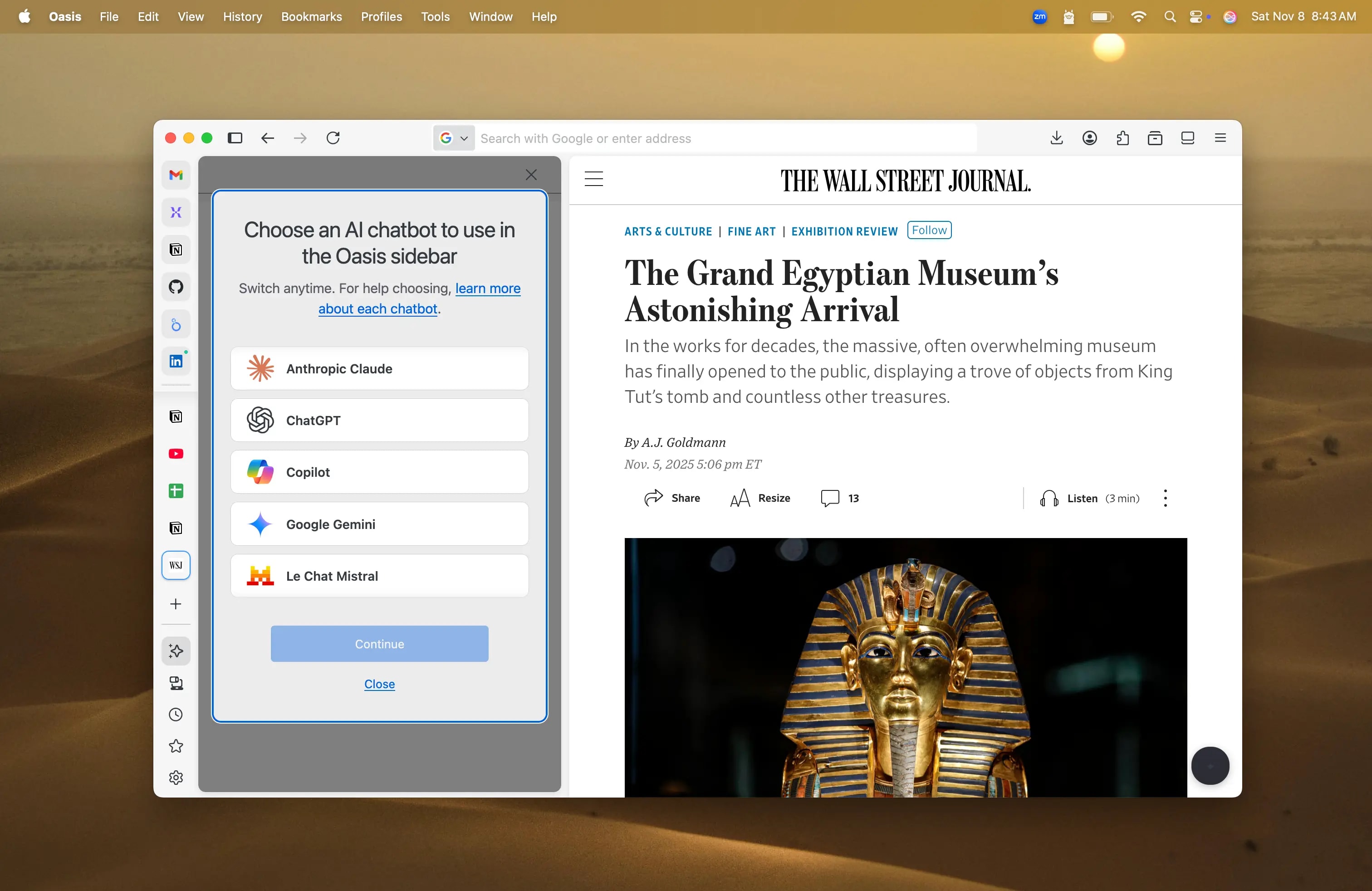
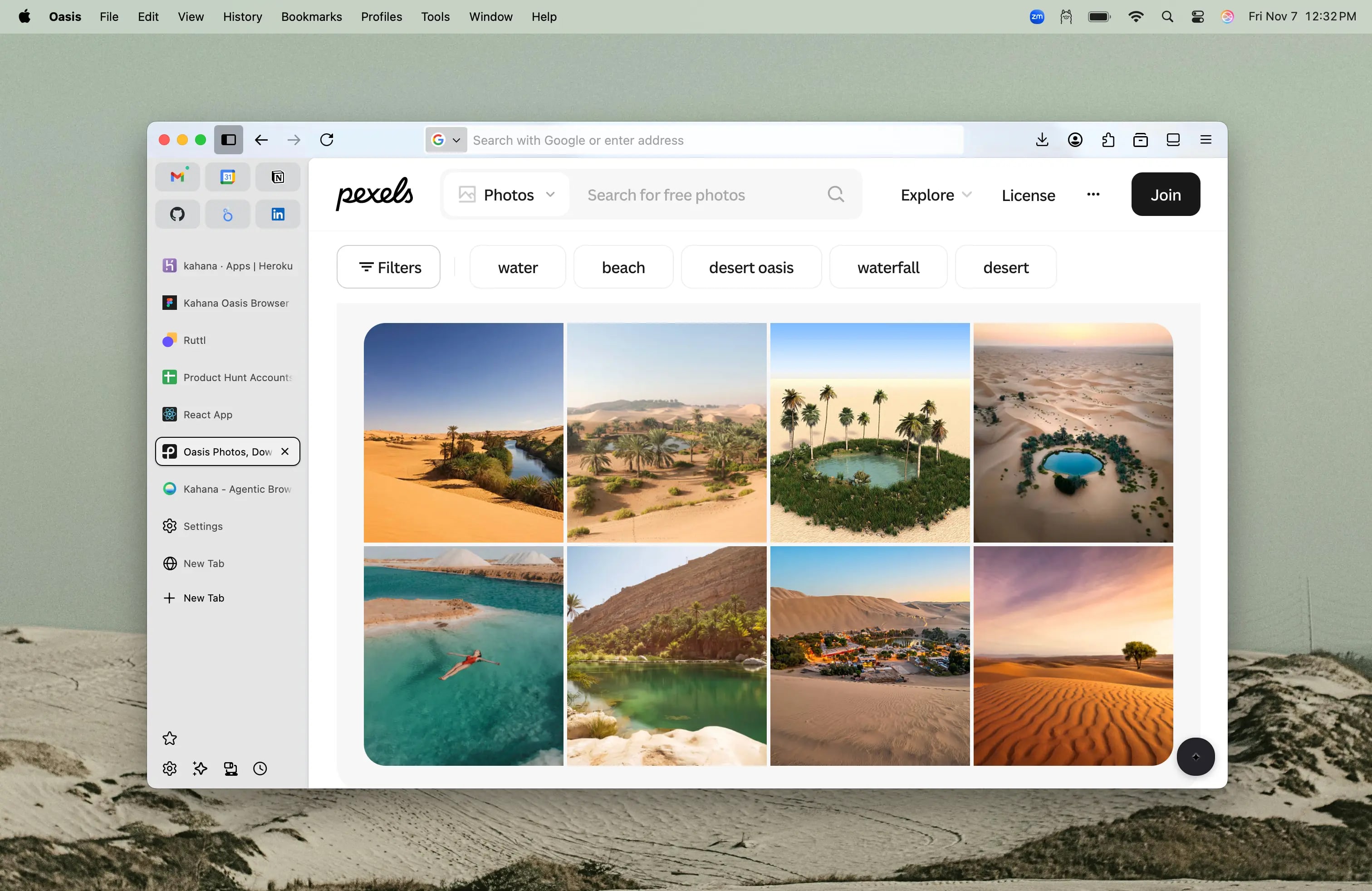
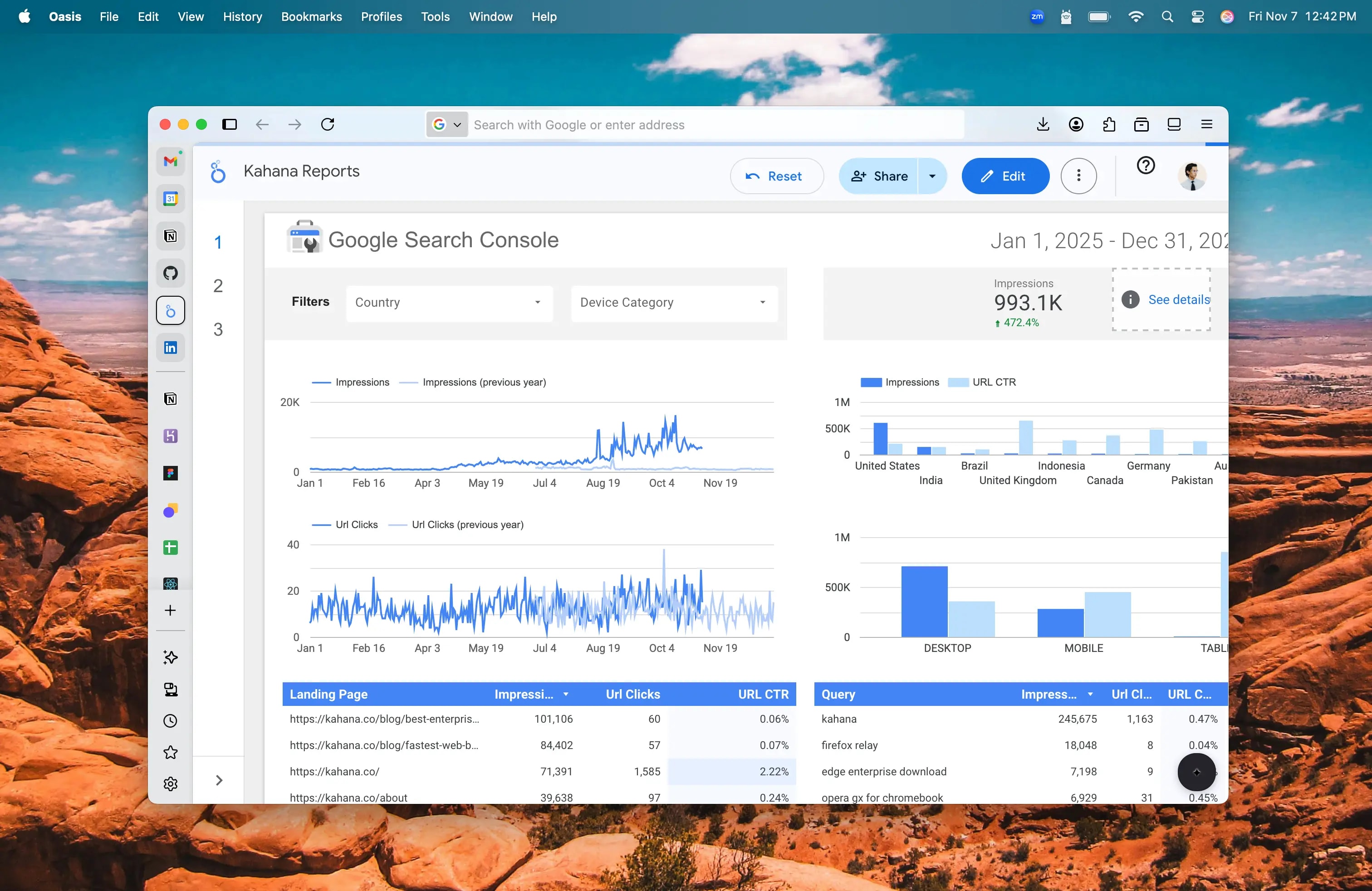
Designed Like an Oasis
A soothing environment that fosters deep work, flow state, and concentration
Oasis represents the first AI browser designed to meld with the way your mind works naturally. Built for ergonomic work, focus, and spatial ease, Oasis creates a soothing environment that is conducive to fostering deep work, flow state, concentration, and focus.
FAQs
Comprehensive answers to technical and business questions
Multi-View
Work with multiple applications simultaneously
Ready to Transform Your Enterprise Browsing Experience?
See Oasis in action and discover how it can revolutionize your organization's productivity and security.